How to set up domain authentication with Twilio SendGrid and Amazon Route53
When you use Twilio SendGrid for sending emails, you have two options to verify your sender addresses:
-
Single sender verification
-
Domain authentication
If you select the first option, you need to confirm you have access to that address by clicking on the confirmation link that will be sent to that address. Domain authentication, however, requires access to the domain’s DNS records. In this article, you will learn how to achieve this when your domain is hosted on AWS Route 53.
Prerequisites
-
A free Twilio SendGrid account
-
An AWS account
You can create a free AWS account, but hosted domains are not covered in Free Tier. A hosted domain costs $0.50 per month, but for testing purposes, you will not be charged if you delete it within 12 hours of creation. For further details, please check Route 53 pricing.
Start Domain Authentication
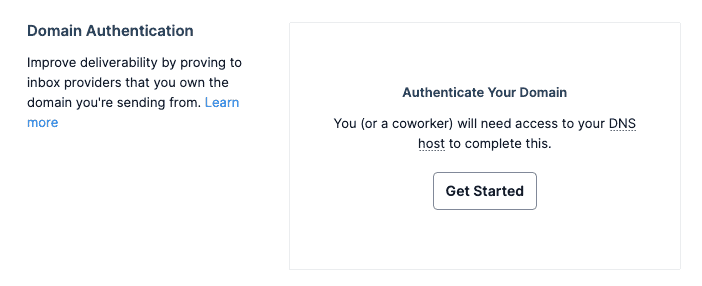
In your SendGrid account, go to Sender Authentication.
Click the Get Started button in the Authenticate Your Domain section:
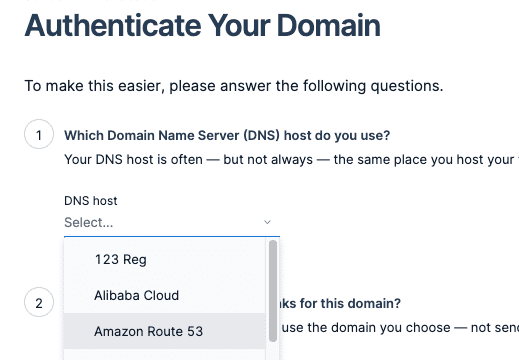
In the DNS host list, select Amazon Route 53:
Leave the branding option as No and click the Next button at the bottom right.
On the next page, enter your domain in the From Domain input:
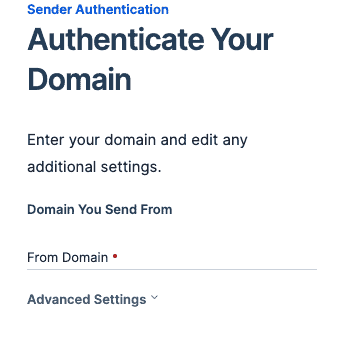
Click Next.
To verify your domain ownership, you will be asked to add CNAME records to your domain:
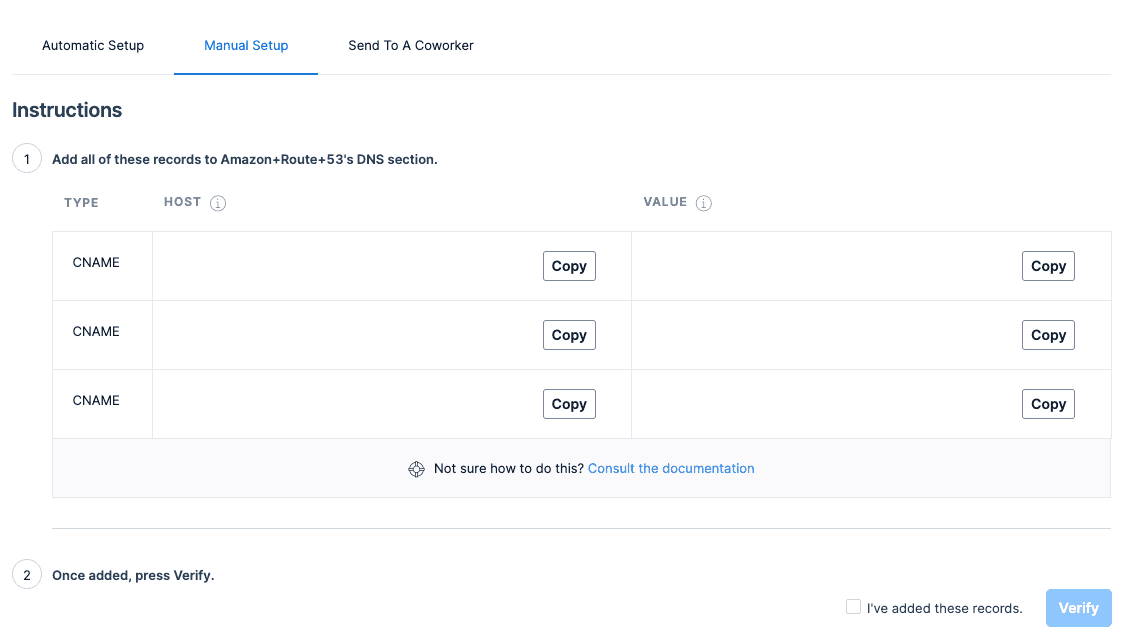
Update DNS Records
Now open the hosted zones in the AWS Route 53 console in another tab.
Click your domain and click the Create record button:
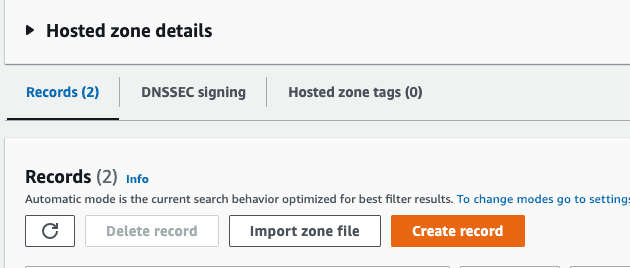
Select CNAME as the record type and enter the name before the domain as the record name.
Then, paste the value in the Value area:
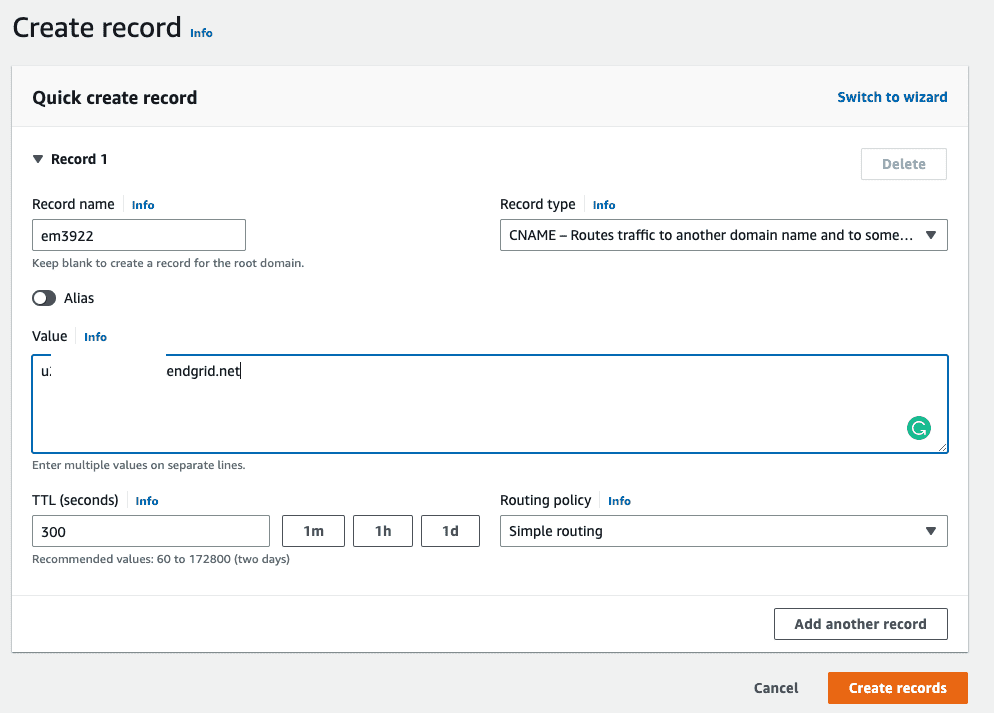
Click Create records.
Repeat this step for all the CNAME records displayed on your SendGrid account.
Verify DNS Records
Now go back to the Install DNS Records page on your SendGrid account.
Tick I’ve added these records checkbox and click the Verify button.
DNS records may take a few minutes to propagate, so it may take a few tries until SendGrid verifies the new entries in your domain.
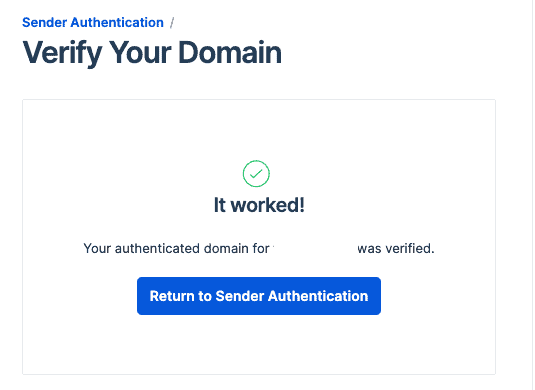
Once done, you should see a success message to confirm your domain has been verified:
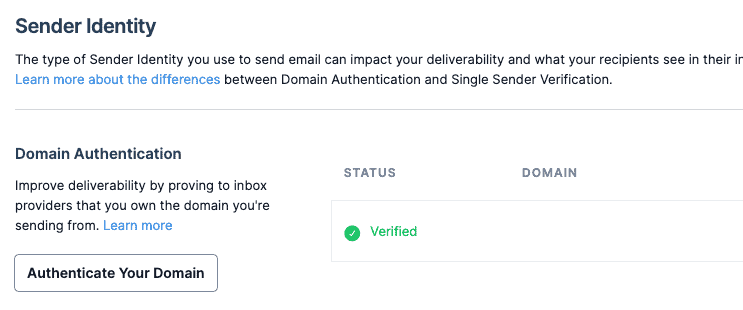
You should see the verified domain on the Sender Authentication page too:
Test sending email
If you already don’t have a mechanism to test your set-up, you can follow the steps below. The example below demonstrates creating a C# console application to send emails. If dotnet is not your cup of tea, you can visit SendGrid documentation for examples in many other languages.
Go to the API Keys page and click the Create API key button.
Give a meaningful name to the key and select Full Access.
Click Create & View.
Click the API key displayed on your screen to copy it to your clipboard. This is your one and only chance to save your key, so make sure to store it in a secure place.
Create a new console application by running the following command:
dotnet new console -o SendGrid.DomainAuthTest
Open the project in your IDE.
Add your API key as an environment variable:
export SENDGRID_API_KEY={your key}
Change to your project folder in the terminal and add SendGrid SDK via NuGet:
dotnet add package SendGrid
Replace the contents of the Program.cs with the following code by replacing the sender and recipient addresses to match your setup:
using SendGrid;
using SendGrid.Helpers.Mail;
var apiKey = Environment.GetEnvironmentVariable("SENDGRID_API_KEY");
var client = new SendGridClient(apiKey);
var from = new EmailAddress("any-address-would-do@yourdomain.com", "Verified Domain Test");
var subject = "This is sent from a random name from the verified domain";
var to = new EmailAddress("{ your recipient address }", "Recipient");
var plainTextContent = "Text content";
var htmlContent = "<strong>HTML content</strong>";
var msg = MailHelper.CreateSingleEmail(from, to, subject, plainTextContent, htmlContent);
await client.SendEmailAsync(msg);
Run the application by running the following command:
dotnet run
You should now receive the test email from the email address you specified.
Conclusion
Verifying the domain may be more cumbersome than verifying a single address, but once you’ve done it, you can send emails from any address you want. Of course, this doesn’t allow you to receive replies which require you to have valid inboxes, which will be discussed in other articles.