Hardening Windows with EMET

EMET (Enhanced Mitigation Experience Toolkit) is a free utility that helps prevent memory corruption vulnerabilities and is designed to prevent hackers from gaining access to a system. I haven’t used it before but according to the documentation the new features are:
- Certificate Trust: Allows to detect Man in the Middle attacks that leverage fraudulent SSL certificates
- ROP mitigations: Block exploit that leverage the Return Oriented Programming exploitation technique.
- Early Warning Program: Allows enterprise customers and Microsoft to analyze the details of an attack and respond effectively.
- Audit Mode: Provides monitoring functionalities for testing purposes.
- Redesigned User Interface: Streamlines the configuration operations and provides accessibility.
Under the hood this tool performs very low-level operations and honestly I don’t know what they all mean. For me the biggest benefit was learning about advanced attacks and exploits and how to avoid them. I strongly recommend reading the user’s guide. Apparently there are many interesting attack techniques when it comes to exploiting the memory. EMET provides mitigation methods against these attacks. For instance:
- Structured Exception Handler Overwrite Protection (SEHOP): This mitigation was shipped with Windows Vista SP1 but with EMET it can be used in previous versions as well.
- Data Execution Prevention (DEP): This mitigation exists since Windows XP but applications need to be compiled with a special flag to opt-in to DEP. With EMET allows applications without that flag to opt as well.
- Heapspray allocation: “When an exploit runs, it often cannot be sure of the address where its shellcode resides and must guess when taking control of the instruction pointer. To increase the odds of success, most exploits now use heapspray techniques to place copies of their shellcode at as many memory locations as possible.”
- Mandatory Address Space Layout Randomization (ASLR): ASLR randomizes the address space of the loaded modules so that attackers cannot predict their locations. Like in DEP, EMET allows applications without the special flag to use this feature.
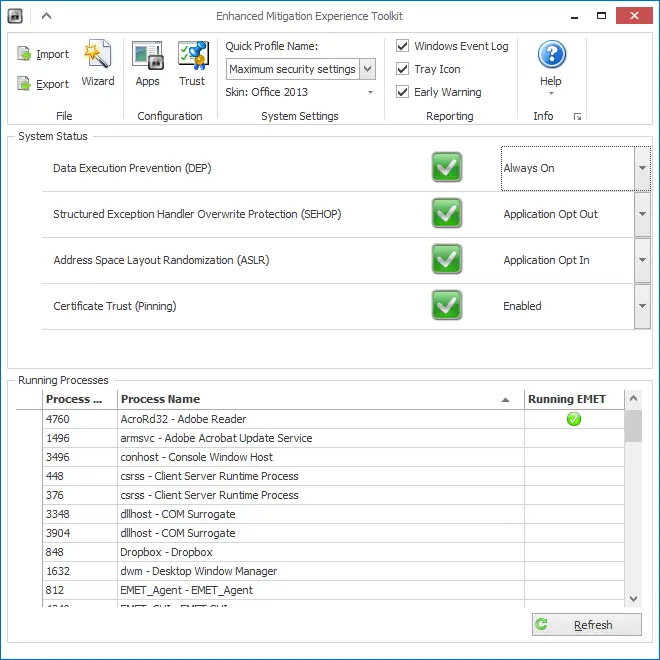
Certificate Trust
I was wondering about this feature as it’s more “visible” than the others. Basically what you do is define protected websites and pinning rules. Pinning Rule is essentially importing an SSL certificate’s thumbprint. Once you import it you create a protected website which is simply entering the domain name of the site and you associate the certificate with the site.
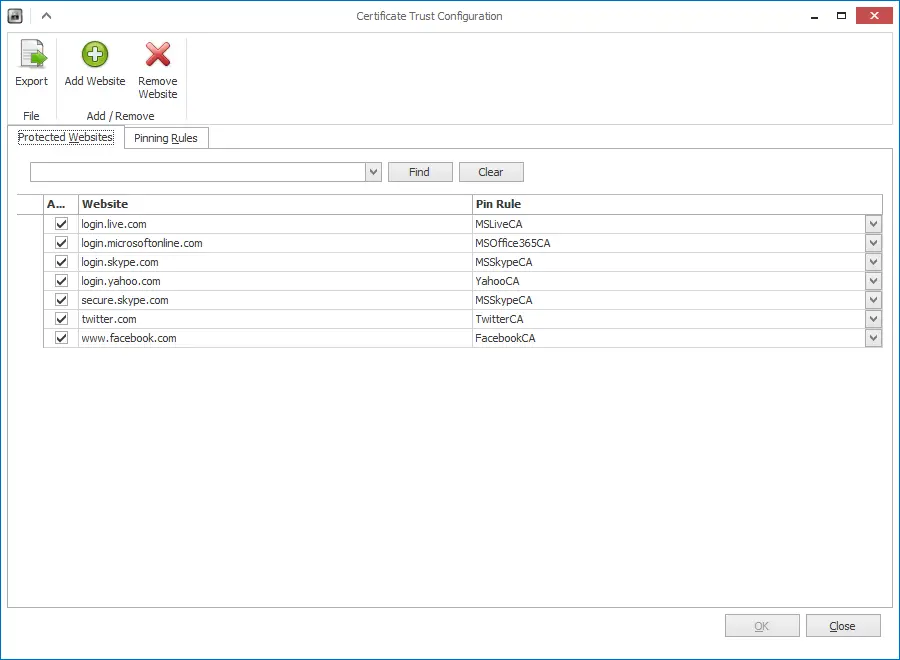
From now on if the certificate changes EMET displays a message like below:
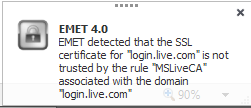
Actually, I didn’t want to spend a great deal to test it first so the easiest way to test is running Fiddler (allow it to install it’s own certificate) and visit login.live.com. EMET comes with that site already configured so as soon as it notices the certificate doesn’t match its rule it fires the alarm. Looks like a nice feature but it only works with IE which I almost never use other than testing my code. Also I was expecting more fuss about it actually. It just displays the window for a few seconds and you can keep visiting the site. If for instance you were looking at something else in that brief period while the site is loading you may completely miss the fact you are being “Man-in-the-Middle”d. Overall, it’s better to have it than not having it at all I think.